Why is Sharing data with Security Automation Only Half of the Puzzle?
In several past blog posts, we have touted the importance of Security Automation as part of any effective Cybersecurity Strategy and Ecosystem. Whether it be leveraging information regarding critical vulnerabilities, threats discovered through DNS or SIEM and SOAR capabilities, tying key systems together to enhance security is crucial.
Although there are seemingly an endless number of integrations available to share data between security systems, the end goal must always be to enhance security. Simply sharing information does not constitute true Security Automation. The goal of automating is to reduce the manual tasks completed by humans to impact an organization in a meaningful way.
Earlier this year, The Enterprisers Project posted a great article, “IT security automation: 3 ways to get started.” On the second page, the third section is entirely dedicated to “Automate enforcement, too”. The author’s main point here is that automation without action is not enough.
“When many organizations start to look at automation, it’s for anomaly detection and to spot intruders on the network. This is a great start, but not enough,” Pitt says. “They should also be looking at automatic enforcement since this will help reduce the workload on the security team.”
Blocking/quarantining users and devices: “Automation can do this many times faster than an engineer,” Pitt says. “Remember that some things that require blocking will be devices, not users. Therefore, should something suspicious be detected, you need it gone in an instant.”
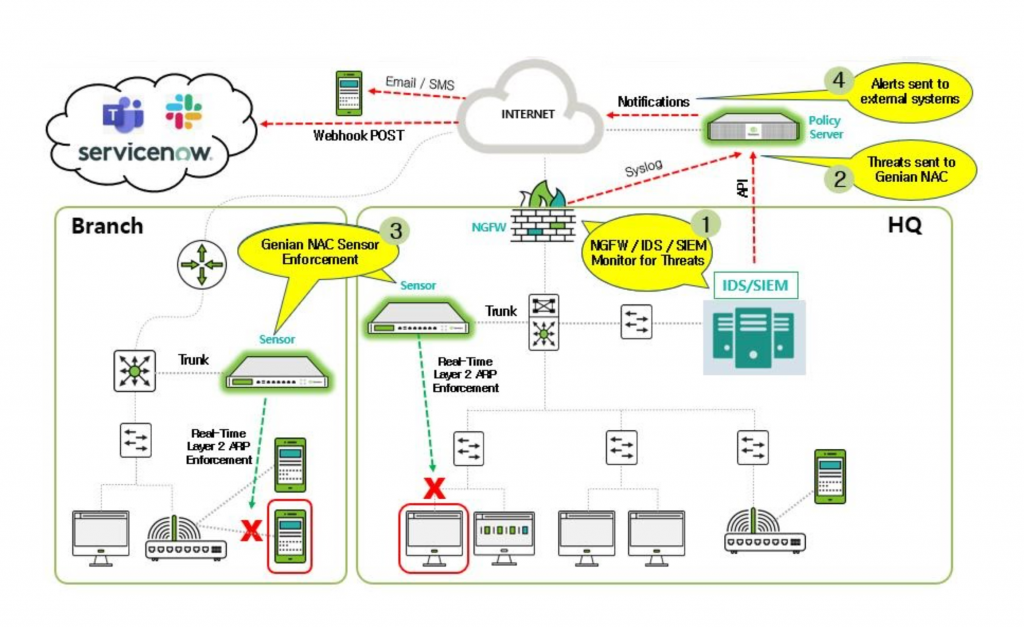
Genians Security Enforcement Automation with IDS, DDI, SIEM, NGFW, and SOAR
Genians shares this philosophy and continues to expand its Security Automation integrations with third-party systems to enhance the security capabilities of the Ecosystem. The latest certified integrations falling under this category include Palo Alto Cortez XSOAR and Beyond Security beSECURE. These join a list of integrations with other platforms such as IBM Resilient SOAR, Seceon aiSIEM, Infoblox DDI, Fireeye, and other systems that allow Genian NAC to perform real-time Layer 2 isolation of threats on the network, without human intervention.
Visit the Genian NAC documentation page today to see how Security Automation in your environment can enhance security, free up resources for other tasks and provide the highest ROI on the components within your Cybersecurity Ecosystem.